TCP OPTIONS
Transmission Control Protocol (TCP) is one of the core protocols of the Internet Protocol (IP) suite. It provides a reliable, connection-oriented communication between two devices over an IP network. TCP includes several options that can be used to customize and control the behavior of the protocol. These options are included in the TCP header and can be negotiated during the TCP handshake when establishing a connection. Here are some common TCP options:
1. **Maximum Segment Size (MSS):** MSS is used to specify the maximum amount of data that can be included in a single TCP segment. It helps optimize the communication by preventing fragmentation, as it ensures that data fits within the Maximum Transmission Unit (MTU) of the network path.
2. **Window Scale:** Window scaling is used to increase the TCP window size. It allows for better performance over high-bandwidth, high-latency connections. The window scale factor is a power of 2 that multiplies the window size specified in the TCP header.
3. **Timestamps:** TCP timestamps are used to improve the accuracy of round-trip time (RTT) measurements and to prevent certain types of attacks. The sender and receiver can include timestamps in their segments to measure the RTT more precisely.
4. **Selective Acknowledgments (SACK):** SACK allows the receiver to acknowledge out-of-order segments and gaps in the received data. It helps improve performance in the presence of packet loss and reordering.
5. **TCP Fast Open (TFO):** TFO is an option that allows data to be sent in the initial SYN packet, reducing connection setup time. It's designed to speed up the opening of short-lived connections, such as those used by web browsers.
6. **Window Size:** The TCP window size, specified in the TCP header, determines how much data the sender can transmit before waiting for an acknowledgment. Window size options, including window scale, can be used to adjust this value.
7. **Urgent Pointer:** The urgent pointer allows a sender to indicate that certain data is urgent and should be processed immediately. It's often used for in-band signaling but is rarely used in modern applications.
8. **Maximum Segment Lifetime (MSL):** This option is used to specify the maximum amount of time a TCP segment can exist in the network. It helps prevent old or duplicate segments from causing issues.
9. **No-Operation (NOP):** The NOP option is used for padding the TCP header when other options are not aligned correctly. It doesn't provide any functionality by itself but is used to ensure proper alignment.
These TCP options can be used to fine-tune and optimize TCP connections for specific network conditions and applications. The negotiation of these options occurs during the TCP handshake, where both the sender and receiver agree on which options to use for the duration of the connection.
*******************************************************************************************
DNS
DNS, or Domain Name System, is a hierarchical and distributed naming system used to translate human-friendly domain names (such as www.example.com) into IP addresses (such as 192.0.2.1) that computers and network devices use to identify each other on the internet. DNS plays a crucial role in making the internet more accessible and user-friendly by abstracting the need to remember complex numerical IP addresses.
Here's how DNS works:
1. **Domain Name Resolution Request:** When you enter a URL (Uniform Resource Locator) into your web browser, such as "www.example.com," your device needs to resolve this human-readable domain name into an IP address to reach the web server hosting the website.
2. **Local DNS Resolution:** Your device first checks its local DNS cache to see if it already knows the IP address associated with the domain name. If it finds a cached entry, it can skip the next steps.
3. **Recursive DNS Server:** If the IP address is not in the local cache, your device sends a DNS resolution request to a recursive DNS server (usually provided by your internet service provider or configured in your network settings).
4. **Root DNS Servers:** If the recursive DNS server doesn't have the IP address, it starts the DNS resolution process by querying the root DNS servers. These root servers have information about top-level domains (TLDs), such as ".com," ".org," and country-code TLDs.
5. **TLD DNS Servers:** The root DNS servers direct the recursive server to the TLD DNS servers responsible for the specific top-level domain in the URL (in this case, the ".com" TLD server).
6. **Authoritative DNS Server:** The TLD server then directs the recursive server to the authoritative DNS server for the domain (e.g., "example.com"). The authoritative DNS server has the specific IP address associated with the domain.
7. **IP Address Retrieval:** The recursive DNS server retrieves the IP address from the authoritative DNS server and caches it for future reference.
8. **Response to Requesting Device:** Finally, the recursive DNS server sends the IP address back to the requesting device. The device can now use the IP address to connect to the web server hosting the website.
DNS operates on a distributed network of DNS servers worldwide, and it is a critical component of the internet's infrastructure. It allows users to access websites and services using human-readable domain names, making the internet more user-friendly. DNS is used not only for web browsing but also for various other internet services, including email, VoIP, and more.
********************************************************************************************
DHCP
The DHCP DORA process refers to the steps involved in obtaining an IP address and other network configuration parameters from a Dynamic Host Configuration Protocol (DHCP) server. DORA stands for Discover, Offer, Request, and Acknowledge, which are the four main stages of this process:
1. **Discover**:
- When a device, such as a computer or a networked device, connects to a network, it first needs to obtain an IP address. To do this, it broadcasts a DHCP Discover message on the network.
- This message is a request for DHCP servers to respond and offer IP address lease options.
2. **Offer**:
- DHCP servers on the network receive the DHCP Discover message and, if available, respond with a DHCP Offer.
- The Offer contains an IP address lease and other network configuration parameters that the server is willing to provide to the requesting device.
- Typically, multiple DHCP servers might respond with offers, and the device chooses one based on certain criteria (e.g., the lease duration).
3. **Request**:
- The DHCP client, after receiving one or more DHCP Offers, selects one of the offers and sends a DHCP Request message back to the chosen DHCP server.
- The Request message confirms the chosen IP address lease and specifies which DHCP server's offer is accepted.
4. **Acknowledge**:
- Upon receiving the DHCP Request message, the chosen DHCP server sends a DHCP Acknowledgment (or Ack) message to the client.
- The Ack message finalizes the process, confirming that the device now has permission to use the offered IP address and other configuration settings.
- The client will use the parameters provided in the Ack message to configure its network interface.
It's important to note that the DHCP DORA process is crucial for automatic IP address assignment in network environments, as it ensures that multiple devices can coexist on a network without manual IP address configuration. Additionally, DHCP can provide other network configuration settings like subnet masks, gateways, DNS server addresses, and more, making it a fundamental service in most modern networks.
********************************************************************************************
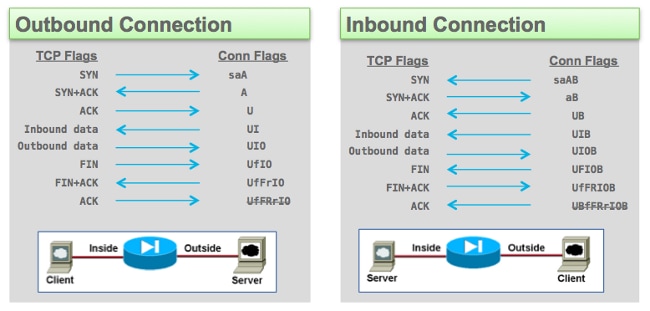
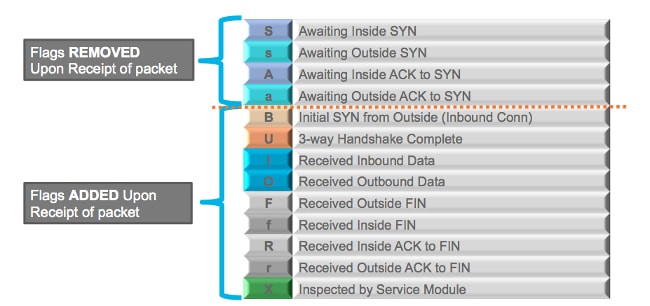
TCP Flags
TCP (Transmission Control Protocol) flags, also known as TCP control flags or TCP header flags, are 6-bit binary values used in the TCP header to control and manage various aspects of a TCP connection. These flags help in establishing and terminating connections, managing data transfer, and handling errors. Here are the six TCP flags:
1. **URG (Urgent Pointer)**: The URG flag is used to indicate that the Urgent pointer field is significant. It is typically set when a segment contains urgent data. The Urgent pointer points to the sequence number of the data that requires urgent processing.
2. **ACK (Acknowledgment)**: The ACK flag is used to acknowledge that the receiver has received and successfully processed the data up to the sequence number indicated in the acknowledgment field. It is essential for reliable data transfer.
3. **PSH (Push)**: The PSH flag is used to request that the data be pushed to the application layer as soon as it is received. It indicates that the data should not be buffered.
4. **RST (Reset)**: The RST flag is used to reset a connection. It is typically sent when a segment arrives on a closed or nonexistent connection. It can also be used to abort a connection in certain error situations.
5. **SYN (Synchronize)**: The SYN flag is used to initiate a new connection. It is used during the three-way handshake process to establish a connection.
6. **FIN (Finish)**: The FIN flag is used to indicate the end of data transmission. It is sent when one side of the connection wants to terminate the connection gracefully. The other side may acknowledge the FIN and also send its own FIN, resulting in a four-way handshake to close the connection.
These flags are set or cleared in the TCP header to communicate the current state and intentions of each side of the connection. The combination of these flags and the sequence and acknowledgment numbers forms the basis for reliable and ordered data transfer in TCP.
********************************************************************************************
OSI Layer
The OSI (Open Systems Interconnection) model is a conceptual framework used to understand and standardize the functions of a telecommunication or networking system. It divides the functions of a network into seven distinct layers, each responsible for specific tasks. These layers are, from the top layer to the bottom layer:
1. **Application Layer (Layer 7):** This layer is the topmost layer and is responsible for providing network services directly to end-users or applications. It deals with issues such as data communication, user authentication, and application-level protocols. Common application layer protocols include HTTP, SMTP, and FTP.
2. **Presentation Layer (Layer 6):** The presentation layer is responsible for data translation, encryption, and compression. It ensures that data exchanged between different systems with different data formats can be properly understood and presented.
3. **Session Layer (Layer 5):** This layer manages the establishment, maintenance, and termination of communication sessions between two devices. It also handles issues like checkpointing and recovery, which are important for maintaining a consistent connection.
4. **Transport Layer (Layer 4):** The transport layer is responsible for end-to-end communication, error detection, and error correction. It ensures that data is reliably delivered between two devices and is responsible for flow control and congestion control. Common transport layer protocols include TCP (Transmission Control Protocol) and UDP (User Datagram Protocol).
5. **Network Layer (Layer 3):** The network layer deals with routing and addressing. It is responsible for routing data packets between different networks and ensures they reach their destination. The Internet Protocol (IP) is a well-known network layer protocol.
6. **Data Link Layer (Layer 2):** This layer handles data framing, physical addressing, error detection, and media access control. It is divided into two sublayers: Logical Link Control (LLC) and Media Access Control (MAC). Ethernet and Wi-Fi are examples of data link layer technologies.
7. **Physical Layer (Layer 1):** The physical layer is responsible for the physical medium over which data is transmitted. It defines the physical characteristics of the transmission medium, such as voltage levels, cable types, and data rates. This layer deals with the actual transmission and reception of binary data.
The OSI model is a theoretical framework and is used to help understand the different functions and protocols involved in networking. In practice, many modern networking technologies and protocols do not neatly fit into this seven-layer model, but it remains a valuable tool for discussing and learning about network communication.